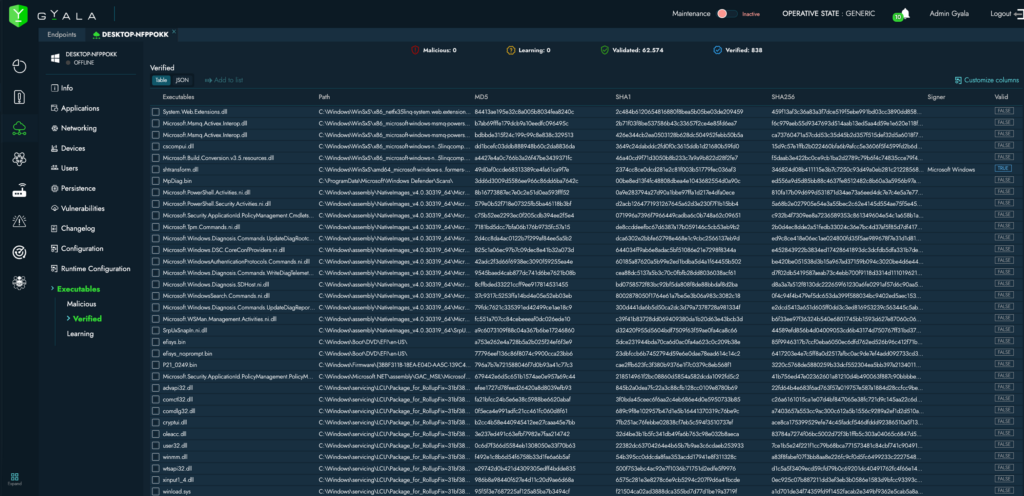
All operating system configurations are constantly monitored, and any changes are recorded in the interface’s change log.
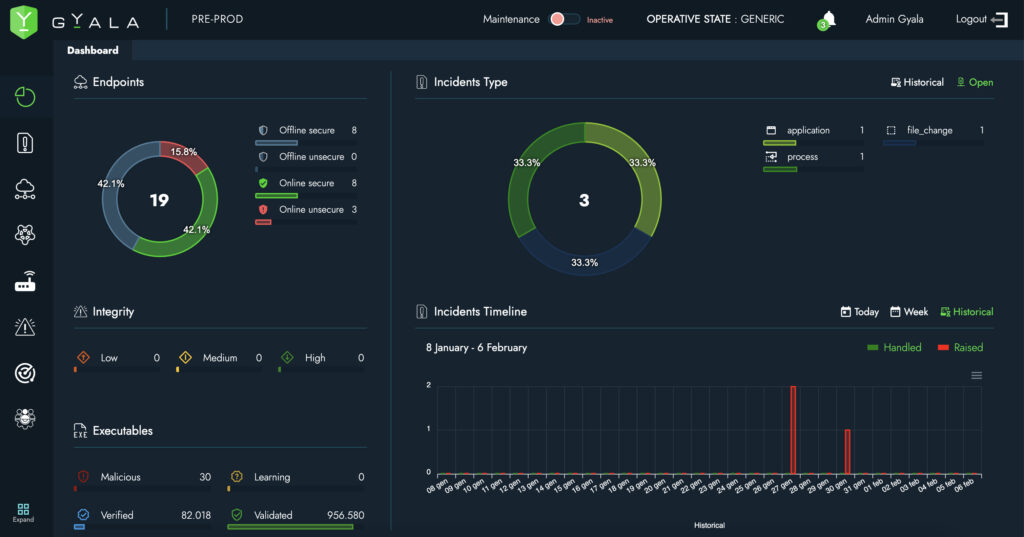
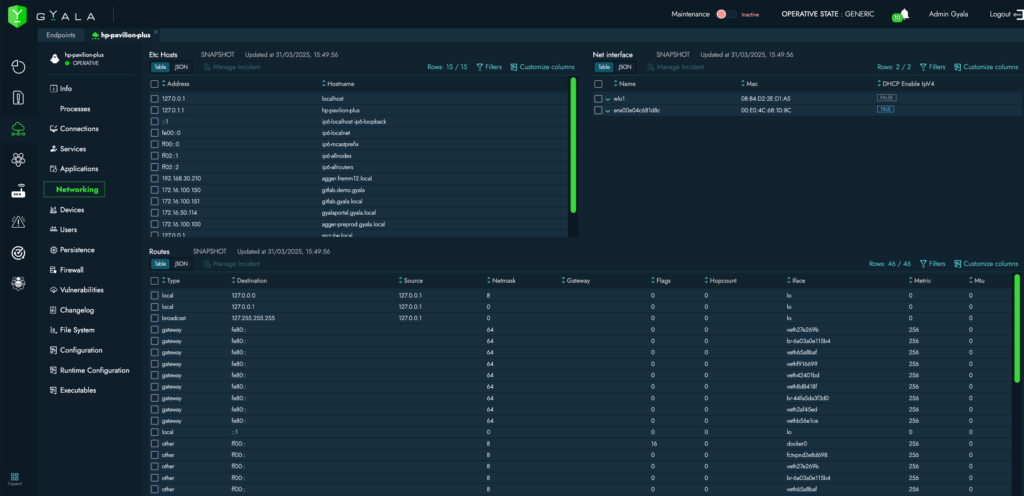
Ability to gather information about the system’s status
at the exact moment an incident occurs, allowing analysts to verify running processes, network connections, logged-in users, routing tables, service statuses, changes to Task Manager configurations, users and groups, network settings, installed software, and more.
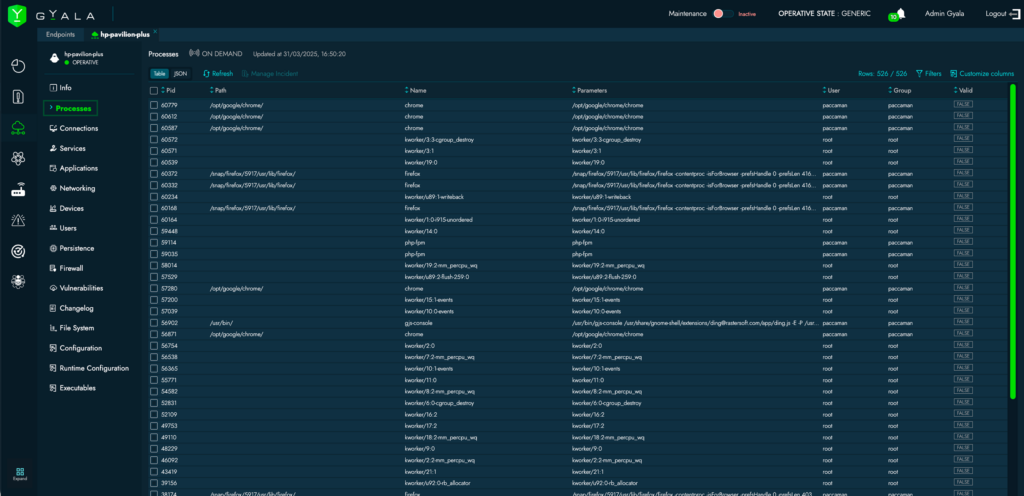
Detailed visibility and real-time control of all running processes
network communications of each process and service, behavior of individual processes and services, modifications to the file system, registry keys, and service configurations across all machines—enabling proactive threat hunting activities.
Advanced Rule Implementation
Starting from Agger version 3.0, detection rules are expressed in Sigma, Yara, and Suricata formats. This makes the detection engine even more flexible, powerful, and granular. The use of these expressive formats improves threat detection and significantly reduces false positives.
Ability to Perform Complex Queries
As of version 3.0, all events, incidents, rules, and centrally collected information on host status, IoT devices, and network traffic can be queried with ease. Users can conduct simple text searches or use Query Domain-Specific Language (OpenSearch DSL) for more precise and faster results.
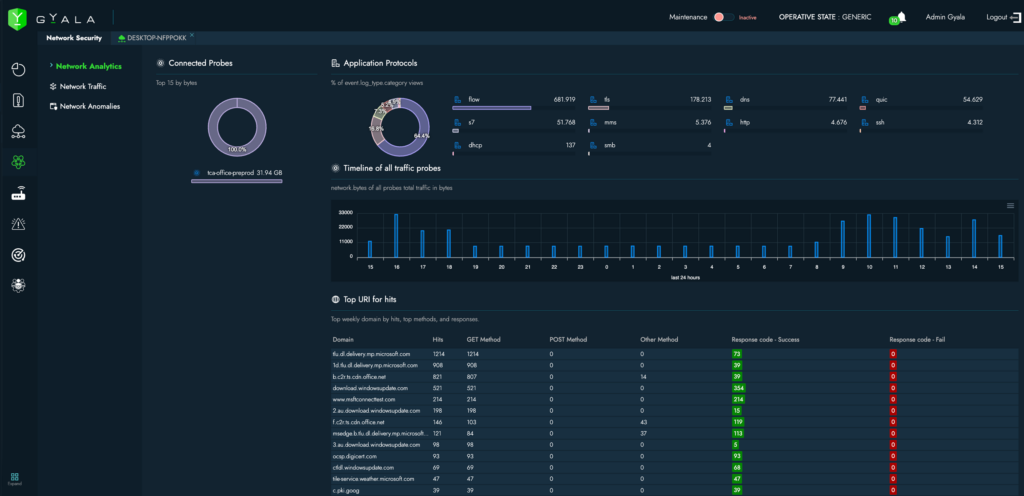
Full Visibility into Network Traffic
From version 3.0 onward, Agger offers improved network traffic visibility and a higher volume of collected data. Logs produced by the probes contain detailed information about every session, including full interpretations of application layer 7 protocols. These are aggregated into dashboards showing macro indicators and can be queried through simple text or DSL searches. The layer 7 data also enables more refined AI-driven behavioral models, enhancing infrastructure understanding and reducing false positives.
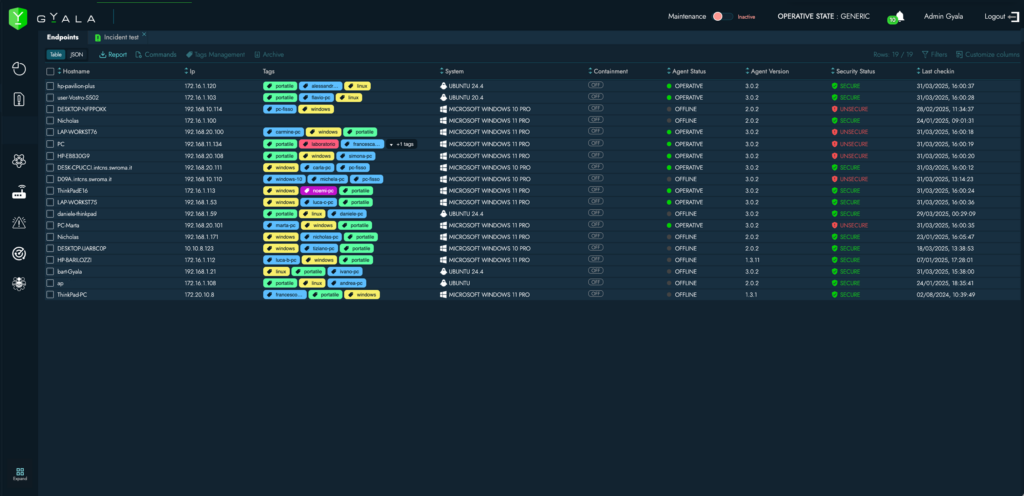
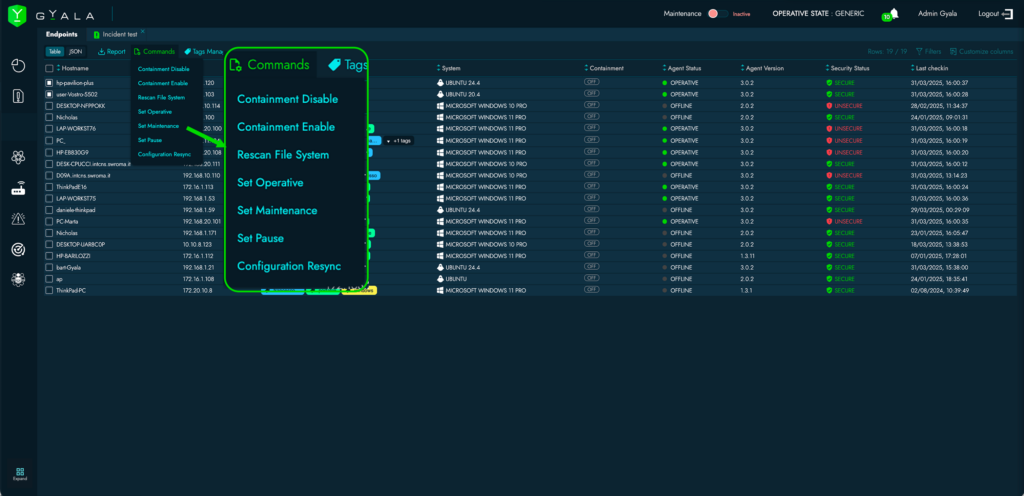
TAG SYSTEM:
The tagging system for endpoints and agentless devices provides critical operational insights about assets, facilitating device identification and incident interpretation.
Tags are fully customizable by the user—there are no restrictions in type or number—and allow the creation of homogeneous groups by type (e.g., server, workstation), service (e.g., emergency room, orthopedics), location (e.g., Building A, 1st floor), or criticality.
Tags can be used in queries or selections to determine which services are impacted, the level of disruption, and where to send personnel for corrective action.
The risk management module also uses tags to define device dependencies or redundancies in service delivery, helping to assess their operational value.
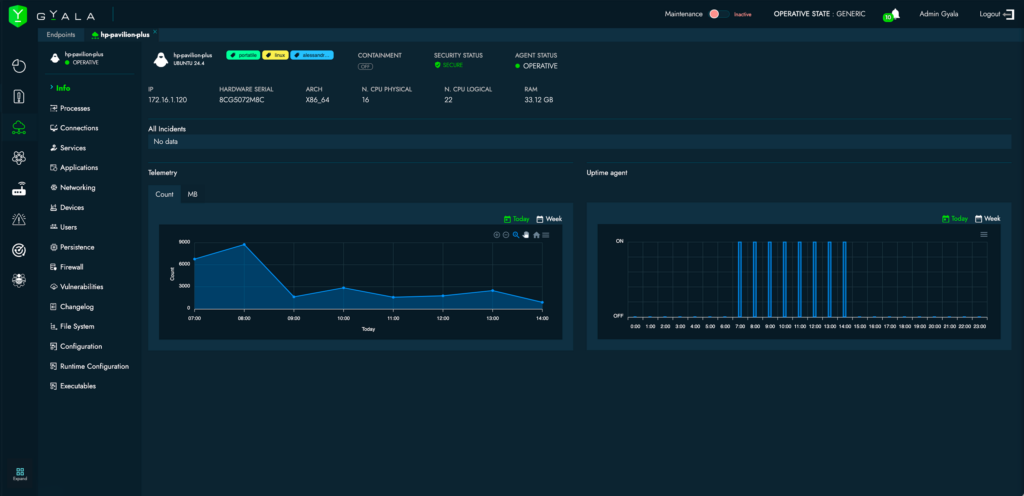
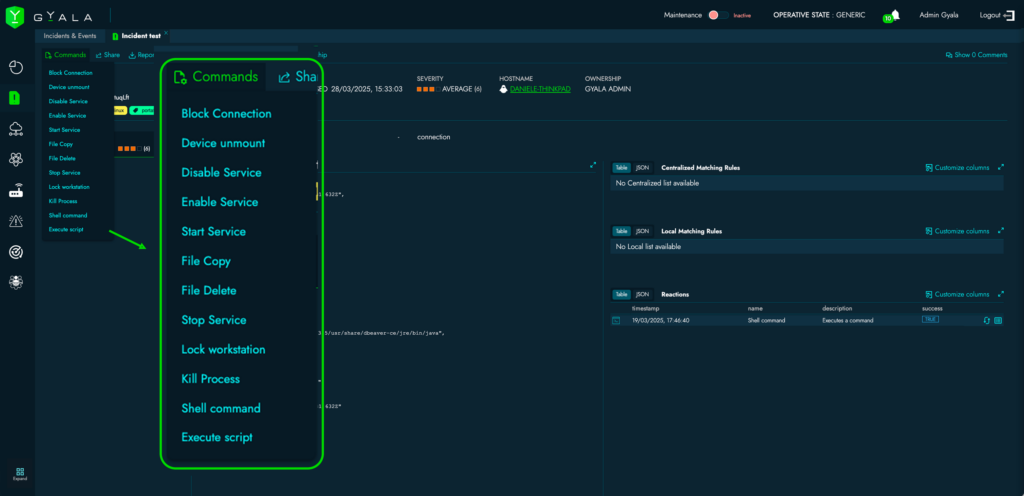
Complete Control from a Single Interface
The Agger console offers real-time visibility into system status and configuration, including:
- Running processes and services, with options to start/stop them;
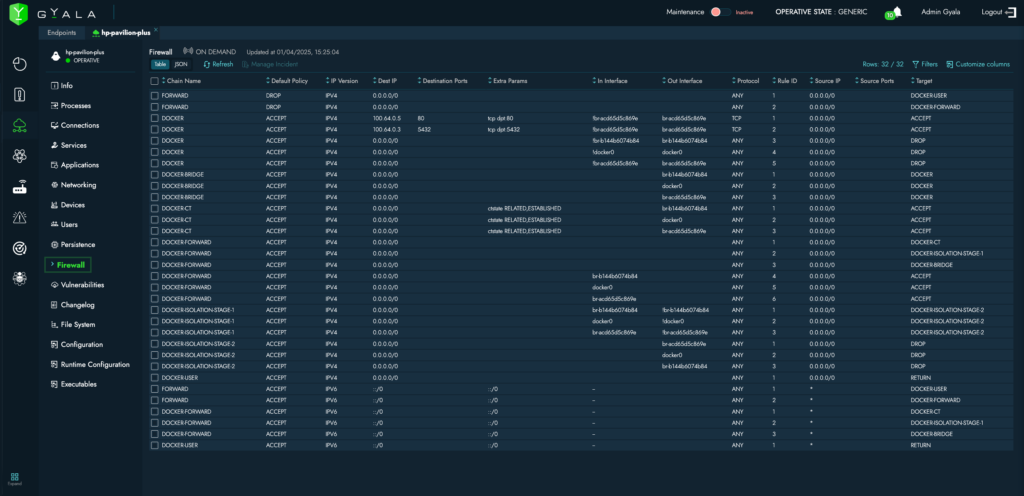
- Real-time network settings and connections per process, with firewall control;
- Full configuration details (users, groups, installed software, missing patches, hardware devices, startup tasks, scheduled jobs, registry keys, and more);
- All OS configuration changes are tracked and logged.
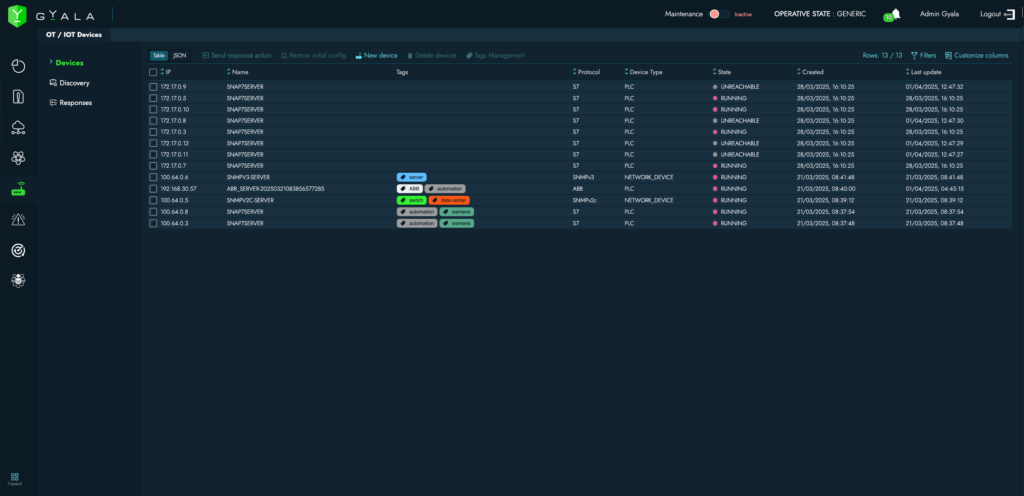
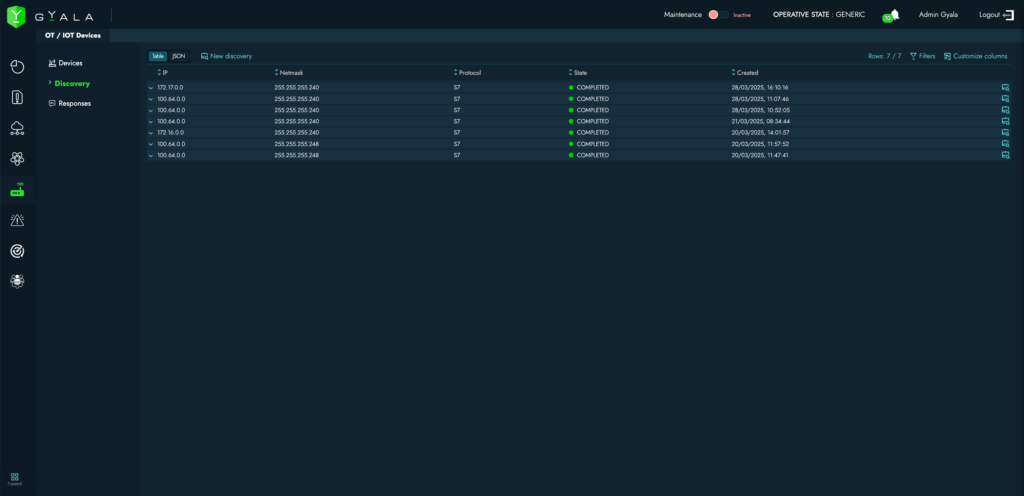
OT/IoT Section
The OT/IoT section allows discovery of PLCs, network devices, medical equipment, CNC machines, sensors, and ECUs. It also enables real-time monitoring of their integrity and availability.
Operators can define specific commands per OT/IoT device and send them directly from the Agger console.
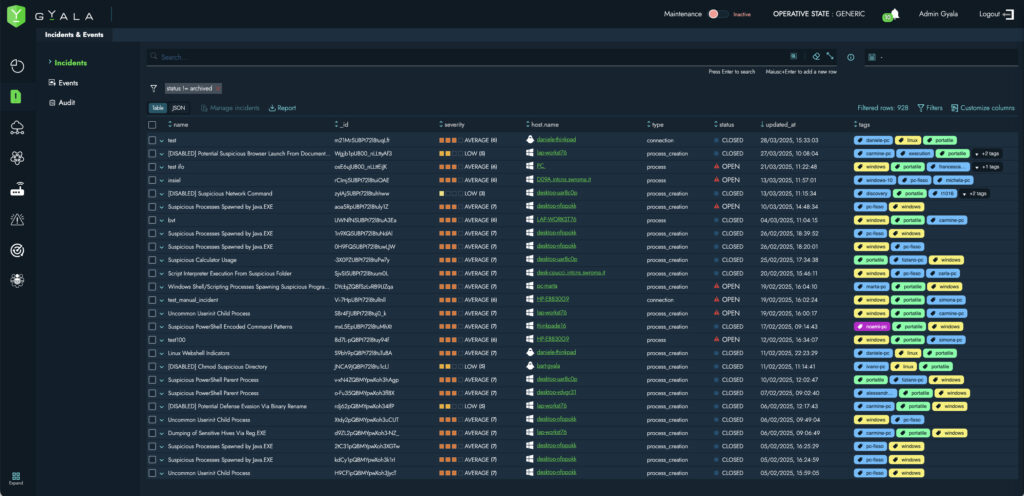
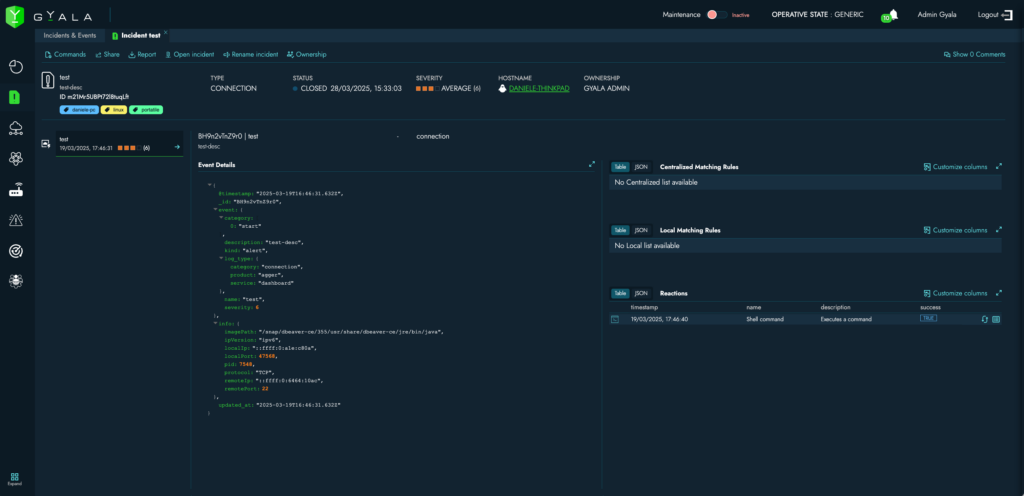
Incident Section
Extensive telemetry data collection and system configuration snapshots, plus the ability to send commands directly to endpoints.
In addition to the detection and reaction events managed autonomously by the agents and sent to the Security Center, telemetry from the operating system (Windows or Linux) is transmitted. This enables attack chain reconstruction (kill chain), deep incident analysis, and supports threat hunting activities.