
IT/OT Convergence: Once Upon a Time There Was Segregation
There was a time when OT operated in a closed world: proprietary networks, vertical protocols, and machines engineered to run […]
Read more
Infostealers Are Not “Just Another Malware”: They Are the New Black Gold of Cybercrime.
Threat Landscape in Numbers: The ACN Assessment Infostealers are not simply another malware family; they are the new “black gold” […]
Read more
Cybersecurity in Manufacturing:
What to keep track of The manufacturing sector continues to be at the top of the most targeted lists: not […]
Read more
How much is your medical record worth?
On the dark web, a single medical record can sell for up to $1,000 Far more than a credit card […]
Read more
LOTL (Living Off The Land)
When the Attacker Uses Your Own Weapons Against You LOTL (Living Off The Land) is a cyberattack technique that stands […]
Read more
The Resilience of Infrastructure Depends on CPS
Source Gartner – Document “Developing a CPS Security Policy Framework Based on Seven Domains”Fonte Gartner
Read more
Mosquitoes and Cybersecurity:
An Unexpected Analogy In summer, we’ve all experienced it: a peaceful evening outdoors… and then comes a mosquito. Silent (until […]
Read more
Cybersecurity 2025:
Six Months That Redrew the Global Risk Map In the first half of 2025, the cybersecurity landscape underwent a profound […]
Read more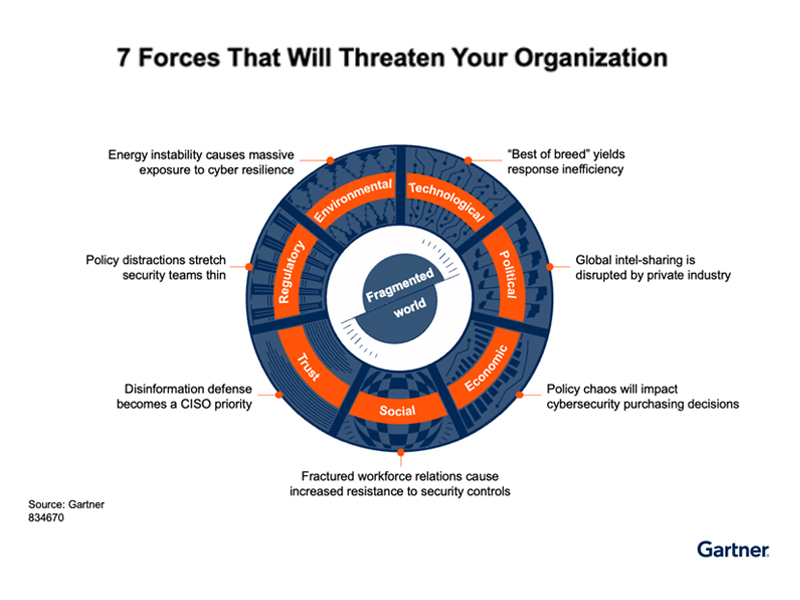
Beyond Technology
The Seven Organic Forces Redefining Cybersecurity Cybersecurity is no longer (just) a technological issue. It is now evident that risks […]
Read more