Protecting Critical Infrastructure in Utilities
A Guide to Achieving a Resilient Approach
What would be the consequences of a disruption in the supply of gas, electricity, or even water?
Such a scenario would have severe repercussions for both individuals and businesses. Depending on the scale and duration, these disruptions could trigger critical consequences.
This is precisely why utility infrastructures are vulnerable to crippling cyberattacks.
Service delivery is the lifeblood of modern society and is deeply intertwined with national security. It is no surprise that cybercriminals see companies responsible for providing and managing essential services as prime targets for their malicious objectives.
Let’s take a closer look at the infrastructure of utility companies and the key challenges they face regarding regulations and cybersecurity:
1) Highly Advanced Threats and Targeted Attacks
Attackers can bypass advanced security measures with the support of state-sponsored groups or criminal organizations. Some of the most dangerous attacks include:
- Global ransomware campaigns, capable of crippling critical systems and demanding multimillion-dollar ransoms.
- Intrusions into Industrial Control Systems (ICS) that can disable power grids or shut down energy generation cycles.
- Tampering with IoT devices, which are often poorly secured and can be exploited to access networks or disrupt smart grid operations.
- Supply chain attacks, where a weak link in a vendor or partner connected to the utility’s network becomes the entry point for cyber threats.
2) Obsolescence and Complexity of OT Infrastructure
Many industrial infrastructures rely on OT (Operational Technology) systems designed decades ago when cybersecurity was not a priority. This creates significant challenges:
- Lack of updates: Many industrial devices do not support regular security patches.
- Integration difficulties: OT systems are not always compatible with modern cybersecurity solutions.
- No network segmentation: Without a proper security architecture, an attack can rapidly spread across various systems.
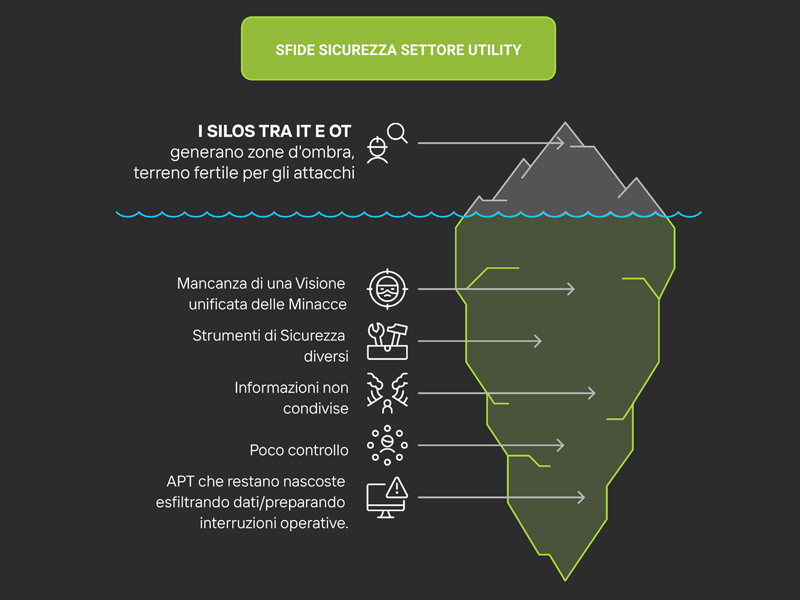
3) Limited Visibility into Threats
One of the biggest challenges in protecting utilities is the lack of a unified view of threats. IT and OT often use separate security tools and do not share information, allowing hackers to move undetected within the network for weeks or even months.
Other critical issues include:
- Excessive security alerts, making it difficult to distinguish critical events from false positives.
- IT and OT silos, complicating coordinated attack responses.
- Advanced Persistent Threats (APTs) that remain hidden for long periods, exfiltrating data or preparing for operational disruptions.
4) Increasingly Stringent Compliance and Regulations
- NIS2 (European Network and Information Security Directive)
- IEC 62443 (Security standard for industrial automation systems)
- National and international regulations
Maintaining compliance without impacting productivity is a complex challenge that requires automated security and compliance management tools.
Gyala’s Solution: Building Cyber Resilience
To address these challenges, utilities must adopt an advanced cybersecurity approach based on:
- Continuous monitoring and real-time threat analysis.
- Automated attack response, reducing reaction times.
- Agentless OT network protection, ensuring security without disrupting industrial operations.
- IT and OT integration, providing full infrastructure visibility.
How AGGER Protects Utilities
AGGER is designed to offer proactive and adaptive security with key features such as:
- Advanced network traffic analysis, detecting suspicious activities before they become concrete threats.
- Automated incident response, with customizable reactions based on corporate policies.
- Security log integration from third-party systems, for a unified event overview.
- OT network monitoring with or without agents, ensuring security without affecting industrial system performance.
- 100% compliance with current regulations, helping companies adopt and maintain best practices in cybersecurity compliance.
The Benefits
- Infrastructure resilience against cyber threats.
- Greater operational efficiency, without compromising security.
- Cost reduction, minimizing financial losses from attacks and reducing the burden on security teams.
- Full compliance with cybersecurity regulations.
Protecting critical infrastructure means adopting resilient solutions that evolve alongside emerging threats. AGGER is a strategic ally for utilities, ensuring security, visibility, and responsiveness in an increasingly complex and regulated landscape.