Health and Cybersecurity: Resilience as an Essential Factor
The Role of IT and OT Cybersecurity in Healthcare
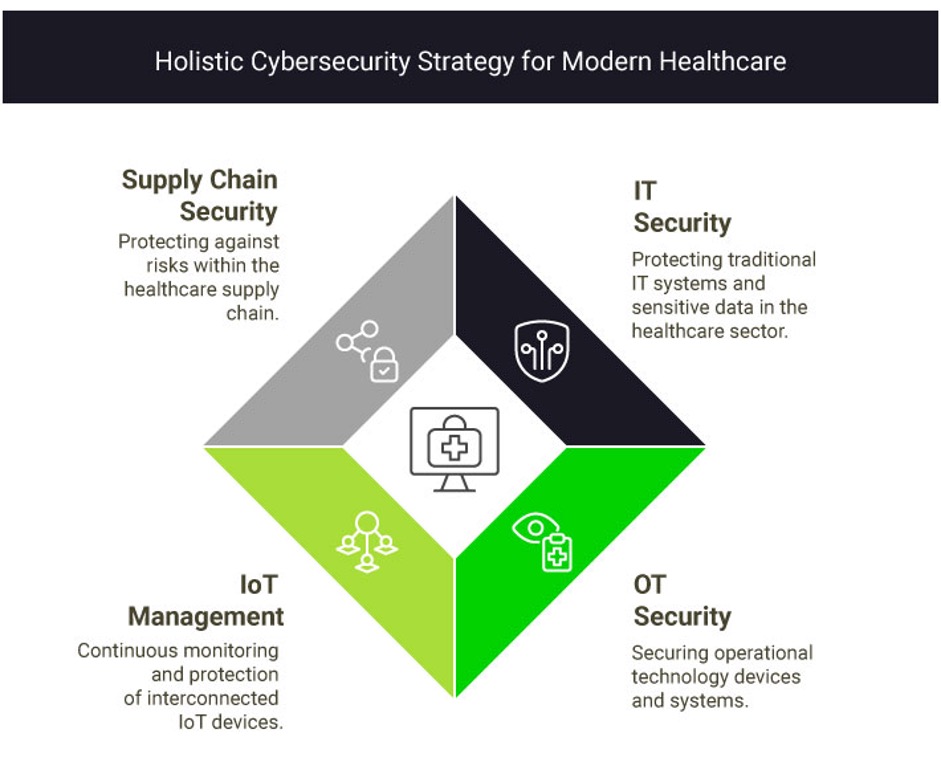
Besides protecting traditional IT systems, it is now essential to consider the security of OT (Operational Technology) environments as well. Devices such as MRI machines, ventilators, and patient monitoring systems are often interconnected, increasing the risk of cyberattacks that could compromise their functionality.
The proliferation of IoT devices in healthcare – such as smart infusion pumps, portable monitoring devices, and surgical robots – has significantly expanded the attack surface. Studies show that nearly 60% of IoT devices still use default passwords, and breaches through these devices have increased by 45% in the past year alone. Many of these devices do not receive proper updates and patches and often lack standardized security protocols. Furthermore, integrating these devices into IT and OT environments creates additional challenges in ensuring continuous security coverage.
To effectively address these issues, a holistic approach is essential. This includes strict IoT device management and the implementation of robust security measures for each device. These devices must be regularly updated and secured with strong, unique passwords. Additionally, they must be integrated within the broader IT security framework to ensure comprehensive protection.
The Supply Chain: The Weak Link in the System
The supply chain is often the primary entry point for cyberattacks. Its complexity—made up of primary, secondary, and tertiary suppliers—introduces risks that are difficult to monitor and mitigate. Every link in the chain can become a gateway for attackers.
Additional Risks:
- Outdated Operating Systems: Often use legacy software, vulnerable to known exploits.
- Unprotected Connectivity: The lack of advanced encryption protocols makes it easier to intercept and tamper with communications.
- Uncontrolled Remote Access: Many devices allow remote maintenance, creating potential backdoors for targeted attacks.
- Dependence on Third-Party Vendors: Lack of visibility into the supply chain’s sub-tier vendors.
- Vulnerable Logistics: Devices may be compromised during transport.
Digital Sovereignty as a Strategic Response:
In this context, digital sovereignty becomes a key concept. Maintaining full control over one’s data, systems, and technological processes without foreign interference is essential. For healthcare organizations, this means adopting solutions that ensure security, transparency, and regulatory compliance.
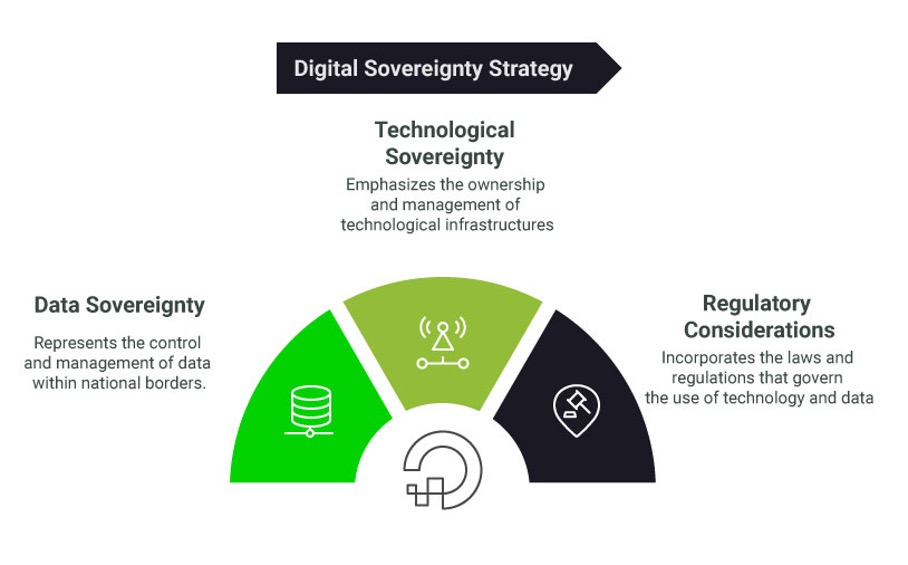
The Digital sovereignty goes far beyond simple regulation. It is based on two essential pillars: data sovereignty and technological sovereignty. To assess the level of control over these key aspects, it is helpful to answer three fundamental questions: where, who and how?
- Where: Refers to the geographical location of the data and the infrastructures that manage it.
- Who: Concerns who can access the data and who owns or controls the technologies that manage it.
- How: Refers to the applicable regulations, i.e., what laws govern the data and the legal restrictions related to the use of technologies.
These topics are regulated by laws already in force. Among them, the GDPR ensures privacy protection; the Data Protection Framework (DPF) regulates the transfer of personal data between Europe and the United States; the NIS 2 Directive defines the rules for cybersecurity of networks and information systems, while the DORA,dedicated to financial services, will come into force in January 2025.
In Italy, the Digital Administration Code (CAD) sets guidelines for the management of data and information by public administration. Organizations such as the: National Cybersecurity Agency,AGID and the Data Protection Authority play a crucial role in managing these complex issues. At the European level, further initiatives are being developed. Among them the Cloud Service Scheme (EUCS) promoted by ENISA, which aims to create certification standards based on the sensitivity of the data processed by cloud providers, and Gaia-X, which aims for a federation of cloud providers based on transparency and security.
Advanced Technological Defense Strategies
1. Zero Trust, detection e reaction automatiche
Adottare un approccio Zero Trust è essenziale per garantire che ogni accesso sia verificato e limitato. La segmentazione delle reti riduce il rischio di propagazione degli attacchi. Essere supportati da una tecnologia automatica, inoltre, permette di rispondere e contenere a tempo zero le minacce, affidando agli esperti di secondo livello il controllo e la correzione della postura di sicurezza
2. Advanced Persistent Threats (APTs) require proactive and predictive technologies to be neutralized. Advanced behavioral analysis, powered by machine learning, plays a key role in identifying deviations in traffic patterns.
3. Resilience While cybersecurity is critical in healthcare environments, resilience is essential: ensuring the delivery of essential services and the functionality of medical devices is a key focus.
What Gyala can do?
We tak about Agger: our platform responds to all these characteristics and thus allows you to create the model of behavior that must assume the IT/OT infrastructure in case of attack, guaranteeing its resilience. We support all legacy systems and are able to reconcile the security needs of the OT world with the flexibility that such a diverse environment requires.
Let’s talk about Agger: our platform responds to all these characteristics and therefore allows you to create the behavior model that the IT/OT infrastructure must assume in the event of an attack, ensuring its resilience. We support all legacy systems and are able to reconcile the security needs of the OT world with the flexibility that such a diversified environment requires.
Conclusions
The healthcare sector is in an unprecedented position of risk, but with the right strategies, it is possible to build a resilient and secure system. Adopting advanced technological approaches, combined with rigorous governance and a focus on digital sovereignty, is the only path to mitigate emerging threats and protect public health in an increasingly digital world.