OT security
Advanced protection for critical infrastructure integrity and continuity
Digital evolution has led to an ever-closer union between IT (information technology) systems and OT (operational technology) systems in all industries. This integration delivers numerous benefits, such as increased process efficiency and higher productivity, but it also brings its challenges, especially in terms of security.
A New Frontier: OT Security
In the past, IT and OT were separate at a technical and organisational level. IT networks were dedicated to managing company data and OT networks handled physical processes, such as production and process control. With the advent of the Industry 4.0 revolution these distinctions have weakened, opening up new opportunities for convergence between the two worlds.
OT system security has become an absolute priority for companies operating in critical sectors, such as manufacturing, electricity, water services and waste management, and it is crucial for ensuring the integrity and continuity of the critical infrastructure that provides the public with essential services and has a significant impact on the economy, such as manufacturing, electricity, water services, and waste management. It is critical to ensure the integrity and continuity of critical infrastructure, which provides essential services to the public and has a significant impact on the economy.
The importance of OT Security
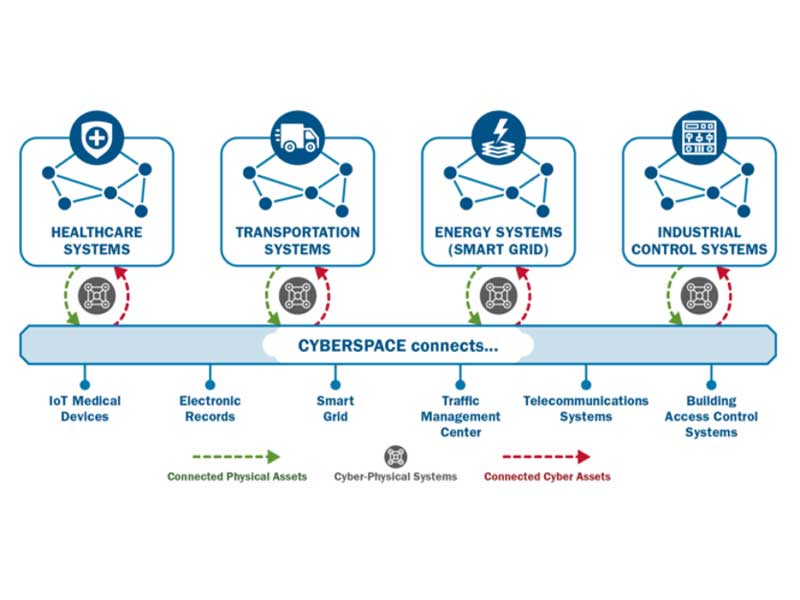
OT security protects industrial systems, such as distributed control systems (DCS), industrial control systems (ICS), supervisory control and data acquisition systems (SCADA), process control (PLC). the Industrial Internet of Things (IIoT), building automation systems (BAS) and physical access control systems (PACS). These systems are essential for the operation of critical infrastructure whose security is of vital importance.
OT security must ensure control in real time, as well as adaptable, available, continuous operation, and data integrity and confidentiality. It must protect the automation systems used to control physical processes, such as emergency services, production plants, transport and the distribution of electricity, water, oil and gas. A security issue in this scenario could result in serious damage, resulting in the suspension of essential services and financial losses.
OT cyber-attacks: A growing threat
In recent years cyber-attacks on OT have risen rapidly. OT systems have become a priority target for cyber criminals, as an attack on these systems can interrupt operations, result in financial loss, and damage the reputation of the companies involved, compromising the safety of people and infrastructure.
According to recent reports, Italy is a victim of 7.6% of the world’s OT cyber-attacks. This figure illustrates the importance of using effective security measures to protect OT systems and prevent potential damage.
The zero-trust approach to OT: An advanced security strategy
To counter increasingly sophisticated cyber-attacks many companies are taking a Zero Trust approach when it comes to OT. This security strategy is based on the principle that no user or device is to be trusted within the network, not even those internal to the organisation. In practice, the zero-trust approach requires every user and device accessing the network to be authenticated and authorised, irrespective of their position or role. Implementing the zero-trust approach for OT demands precise planning and the use of advanced security solutions.
Agger – The All-in-One OT security platform
To guarantee OT system security it is essential to use advanced security solutions, such as the Agger platform.
Agger delivers cutting-edge technology to protect IT/OT environments. This platform uses artificial intelligence algorithms to detect irregular behaviour in network traffic and processes, guaranteeing the stability and resilience of IT/OT infrastructure.
Agger’s main features include:
- Detection: Using artificial intelligence algorithms to detect irregular behaviour in network traffic and processes.
- Orchestration: Continually analysing the status and configuration of each client, server and device in the IT/OT infrastructure and applying detection and reaction rules globally and at each individual endpoint.
- Reaction: Automatically applying counterattacks in real time based on knowledge of the infrastructure and the services it provides. Reactions can be configured by the customer, even at individual agent level.
- Investigation: Gathering and summarising information on the behaviour of the monitored infrastructure and making it available for analysis by experts.
Agger is a flexible platform that adapts to any type of device or operating system. It also supports legacy systems and can be implemented in the cloud, on-premises, or on segregated networks depending on company requirements.
Conclusions
OT security has become an absolute priority for organisations operating in critical sectors. Cyber-attacks on OT are rising rapidly and they can cause significant damage, resulting in financial loss and compromising the safety of people and critical infrastructure.
Companies are using advanced solutions to protect their OT systems, such as our Agger platform.
OT security is a complex challenge, but by using advanced solutions and having a well-defined security strategy, organisations can protect their critical infrastructure and guarantee operational continuity.